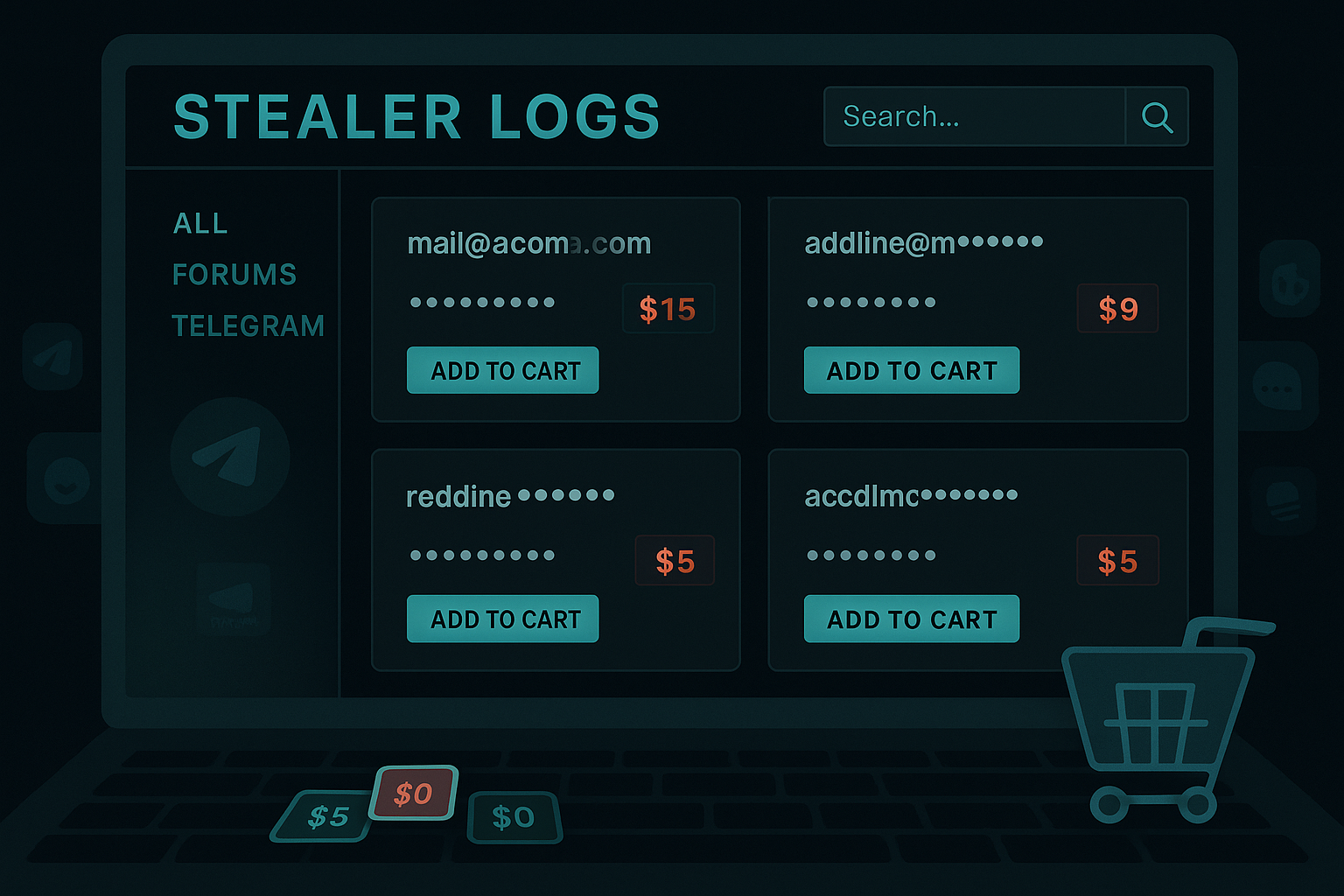
Every year, billions of login credentials and session cookies get traded on underground platforms. In 2024 alone, infostealers grabbed 2.1 billion credentials, representing nearly two-thirds of all credentials stolen that year.
Meanwhile, device infections from data-stealing malware have surged. In 2023, nearly 10 million devices were affected, representing a 643% increase over the previous three years.
In this article, we’ll take a look at exactly what stealer logs are, how they’re generated, what’s inside them, and why they matter for both individuals and enterprises.
You’ll also see real-world examples, common misconceptions, and the defenses that actually work against them.
What Are Stealer Logs?
A stealer log is a record of data that “infostealer” malware lifts off an infected computer or phone and uploads to a criminal server. Malicious actors often call these records “logs.” Each file contains all the information the malware scraped in a single sweep.
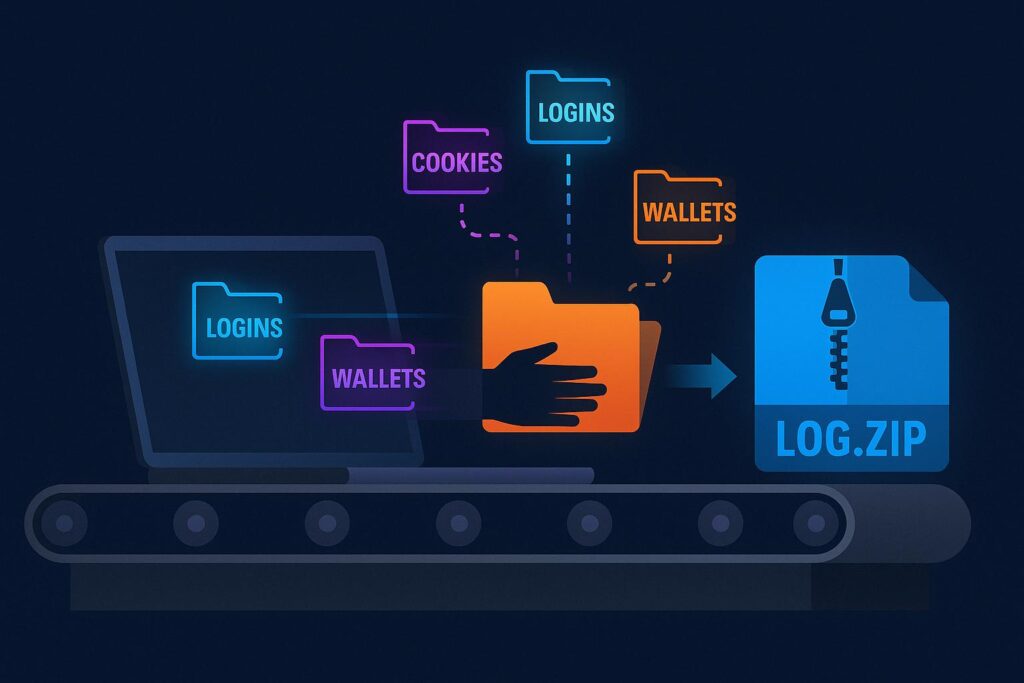
In practice, the log is a package of files (often a ZIP or text dump) that contains all the personal data the malware could harvest, principally saved login credentials, cookies, and other sensitive information from the victim’s system.
Once the haul lands on a criminal server, threat actors sort, bundle, and trade these logs on Telegram channels and dark-web markets.
Underground market research suggests the scale is massive, with tens of billions of stolen cookies circulating in 2025, and approximately 42 billion of those were tied to the RedLine stealer alone.
Session cookies are prized because they let attackers jump straight into a live account without a password or MFA prompt.
From there, they can empty cards, drain crypto wallets, seize cloud dashboards, or impersonate employees in email threads.
Because logs mix personal data with payment info, sellers re-package the same victim’s files many times: a cheap raw bundle today, a “premium” slice with fresh corporate credentials tomorrow.
What Is a Stealer?

A stealer is malware built to pull saved data off a device and send it straight to an attacker-controlled server. It runs quickly, copies the stolen data, and leaves little trace.
Attackers drop stealers through phishing emails, search-ad malvertising, and rigged “free” or cracked software installers. These channels dragged millions of users into stealer campaigns during 2024-2025.
This scale is possible because the theft process is now fully automated, and the rise of Malware-as-a-Service (MaaS) allows even non-technical criminals to rent ready-made stealers complete with dashboards and support.
Among the most prolific of these stealers are:
- RedLine Stealer – the widest spread; sells for approximately $100-$150 on Telegram and dark web forums.
- Vidar – lifts browser credentials and full crypto-wallet files; operators also rent it to drop other malware.
- LummaC2 – subscription kit tied to recent FBI/CISA bulletins; steals multi-factor tokens and pushes follow-on payloads.
- Raccoon v2 – back on sale after a 2023 pause, priced around $275 per month; grabs passwords, cookies, and wallet seeds.
- StealC v2 – advertised for roughly $200 per month, adds stealth upgrades and a click-to-build control panel.
Because these kits are so widely available through the MaaS model, their low cost and one-click setup have led to a dramatic rise in stealer attacks year after year.
How Stealer Logs Are Generated
A stealer lands through a phishing mail, a rogue ad click, or a cracked software installer. Once active, RedLine and similar strains trawl browsers, mail apps, wallets, and autofill stores, writing each catch to plain .txt or .json files in a temp folder.
The malware then compresses every file into a single archive, often named Log.zip, or packed as .rar, and immediately sends it to its command-and-control server.
On the attacker side, Telegram bots or open-source parsers instantly receive and unzip the haul. They convert the raw data into structured JSON and automatically tag logins by site, card brand, or wallet type.
Fresh archives then move rapidly to markets such as the Russian Market, where vendors list them within minutes for just a few dollars.
Essentially, from an infected machine to a sale listing, the path looks like this:
infected host → RedLine (or another stealer) → C2 server → packaged log → parser bot → Russian Market post.
This fully automated chain, plus low rental fees for stealers-as-a-service, keeps the trade brisk and profitable.
What’s Inside a Stealer Log?
A single stealer log contains everything the malware can grab before it transfers the archive to the attacker’s server. The stolen data usually falls into five clear categories.
Data type | What it holds | Why hackers want it |
Web-browser data | Saved passwords, cookies, credit-card numbers, and autofill text | Log in fast and shop with the victim’s cards |
Email data | Contacts, calendar events, file attachments | Send fake emails to trusted contacts and find new targets |
App data | Social-media tokens, chat app sessions, full crypto-wallet files | Steal funds and pose as the user on popular platforms |
System details | Device name, IP address, OS build, hardware list | Spot high-value machines and tweak attacks to dodge security tools |
Session tokens | Live cookies and API refresh tokens | Skip passwords and MFA to enter accounts that are already signed in |
Because the archive combines personal data, payment details, and live tokens, sellers can slice the same log into different price tiers, such as “raw dump,” “premium corporate set,” or “crypto-only,” and resell it multiple times.
Real-World Examples: RedLine Logs in Action
- Low entry cost – Underground forums sell a RedLine subscription for about US $100–150, complete with builder and updates.
- Cookie theft beats MFA – Sellers import session cookies from RedLine logs into a browser plug-in, then sign straight into corporate VPN or Citrix portals without a new MFA prompt.
- Crypto wallets drained – In one 2022 scam, RedLine scanned victims’ disks for wallet files, exfiltrated them, and helped thieves strip millions in coins.
- Logs are dirt-cheap – Initial-access brokers push individual RedLine logs on markets like Russian Market for just US $5–20, so even first-time fraudsters can buy fresh credentials.
The Underground Marketplace for Stealer Logs
Within hours of exfiltration, stealer logs surface for sale across dark web forums, specialist markets, and invite-only Telegram channels.
Major marketplaces include Genesis Market (before its April 2023 takedown), Hydra, Russian Market, Exodus, and 2Easy Shop.
Many of these platforms mimic the familiar search interfaces of Amazon or Google, letting buyers filter by company, country, or service to find the exact data they need.
Stealers now peddle both raw logs and “processed” data. On forums and Telegram, sellers often post free samples to showcase their product, while premium channels offer subscribers fresher batches for $200–$500 per month.
Prices vary: raw logs can sell for as little as $1 to $25, while highly sensitive data commands a steep premium.
The main buyers fall into three groups:
- Cyber-criminals who want instant access to bank, email, cloud, or social accounts.
- Other threat actors who buy logs in bulk, sort the contents, and resell smaller, high-value bundles at a markup.
- Ransomware operators looking for a quick foothold inside corporate networks; they purchase logs from initial-access brokers and then launch their malware.
Common Misconceptions
“All data in stealer logs is fresh.”
One of the biggest myths is that every credential in a stealer log is brand-new. In reality, logs often contain stale or recycled data.
Threat actors may mix fresh exfiltrated information with old leaks to bulk up the size of their offerings. Some even insert completely fake records to boost the appeal of their samples.
For security teams, this means a log entry with your company’s email doesn’t always point to an active breach; sometimes, it’s just old information that’s being resold for the tenth time.
“If my credentials are in a log, my company was hacked.”
Finding corporate credentials inside a stealer log doesn’t automatically mean the corporate network was breached.
In many cases, the infection happens on a personal device that an employee used to log into work systems. For example, an employee might have checked their email on their home laptop that’s infected with malware, and the stealer captured their login.
So essentially, the company may not have been directly attacked, but there’s still risk because the exposed credentials could be reused against corporate accounts.
“Stealer logs always equal immediate compromise.”
It’s easy to think that if your credentials appear in a log, an attacker already controls the account. That’s not always true.
- If multi-factor authentication (MFA) is in place, stolen passwords alone may not be enough.
- If users rotate or reset passwords regularly, the stolen credentials may already be invalid.
- Some logs get delayed in distribution, so by the time they’re sold, the data could already be useless.
That said, ignoring these logs is still dangerous. Even with MFA, exposed data can be used for phishing, social engineering, or brute-force attempts.
The right response is swift mitigation with password resets, MFA enforcement, and close monitoring, rather than assuming compromise is automatic or, worse, dismissing the risk.
Why Stealer Logs Are Dangerous for Enterprises
Stealer logs might look like just another dump of stolen data, but the reality is far worse. For enterprises, they open multiple doors to attackers, each one carrying its own kind of risk:
- Phishing-Ready Data: Stealer logs don’t stop at usernames and passwords. They often include autofill records, browser cookies, and even company-specific details. Attackers can use that context to craft phishing lures that appear frighteningly authentic, such as fake Zoom invitations or invoice follow-ups. With ready-made data, the odds of a successful click increase significantly.
- Account Takeover: Business email compromise (BEC) depends on valid credentials, and stealer logs deliver them instantly. Once inside an inbox, attackers can reroute payments, impersonate executives, or spread malware. Instead of wasting time on brute-force attacks, criminals skip straight to exploitation with working logins.
- Supply Chain and Lateral Risk: Contractors, vendors, and third parties often bridge into enterprise systems. If their devices are infected, attackers can use stolen credentials as an entry point into a larger network. That single weak link can be enough to spread laterally and put the entire organization at risk.
- Family Member Exposure: Executives aren’t the only targets. A spouse or child using the same home Wi-Fi or borrowing a work laptop could unwittingly leak credentials through a stealer. For attackers, that’s an easy way to pivot into corporate access without ever directly breaching enterprise defenses.
How to Defend Against Stealer Logs

Here are some great ways both individuals and organizations can defend against stealer logs, from everyday habits to enterprise-level safeguards and specialized tools.
Individual and Employee Defenses
For many breaches, the weakest link is an everyday user. Employees can cut their exposure dramatically by following a few best practices:
- Avoid browser storage for credentials and rely on a trusted password manager instead. Saved logins in browsers are prime targets for infostealers.
- Turn on phishing-resistant MFA (such as hardware keys or app-based authenticators). This makes stolen passwords far less useful.
- Keep your software updated and avoid downloading cracked versions. Outdated or pirated software is one of the easiest ways for stealers to slip in unnoticed.
- Check exposure regularly through HaveIBeenPwned or similar services so leaked accounts can be reset before threat actors exploit them.
Organizational Defenses
Enterprises need layered protections that account for both scale and sophistication. Beyond basic hygiene, the following measures are effective:
- Dark web monitoring to detect when employee or customer credentials surface in stealer logs.
- Data broker removals to strip down the personal context criminals use to sharpen their phishing lures.
- Session and token hygiene with shorter lifetimes and forced reauthentication reduces the value of stolen cookies or tokens.
- Email filtering tuned to stealer-related lures — such as fake software updates or cracked downloads — catches threats before users click.
- Zero Trust and least privilege ensure that even if one credential is stolen, attackers can’t move freely across systems.
- Linking to related client services (like threat intelligence or fraud prevention solutions) creates a unified response strategy.
VanishID’s Role
Technology can close gaps where policies and human behavior fall short. VanishID strengthens enterprise defense by:
- Detecting employee and executive credential exposure as soon as it hits circulation.
- Automating dark web and stealer log monitoring, so threats are identified early.
- Driving remediation, from forced resets to takedowns, limiting the shelf life of stolen data.
Protecting executives’ family members, covering those “side doors” that attackers often exploit for indirect access.
The Future of Stealer Malware
Stealer malware continues to spread, but now with stealthier tactics and more organized operations. That said, here are some great trends already shaping where things are headed:
AI-Assisted Infostealers
Developers are starting to experiment with AI to make stealers more adaptive and harder to detect.
Think polymorphic code that constantly changes its signature, or malware that learns user behavior to avoid raising red flags. This could render traditional defenses, such as signature-based antivirus, far less reliable.
Expansion of Marketplaces with Subscription Models
Criminal marketplaces are shifting to a subscription economy. Instead of one-off log sales, we’re seeing premium “data as a service” models where subscribers pay monthly for fresh batches.
This predictable revenue stream enables these markets to operate more like SaaS businesses, which in turn funds further development and resilience.
Integration with Ransomware and Phishing Groups
Stealer logs are increasingly feeding directly into larger attack chains. Ransomware crews buy them for footholds inside corporate networks, while phishing groups use the data to build more effective lures.
This tight integration means stealers are no longer just an entry-level cybercrime; they’re becoming the backbone of multi-stage attacks.
Final Thoughts
Stealer logs are the fuel behind a wide range of today’s cyberattacks. They give criminals the raw material for phishing, account takeover, and ransomware, making them far more than just another data leak.
Grasping how these logs are created, traded, and abused helps defenders respond with clarity and control. Strong authentication, a smaller digital footprint, and proactive monitoring all work together to blunt their impact.
VanishID brings these defenses into focus by monitoring stealer log circulation, detecting exposure early, and cutting off attacker leverage before it turns into a breach.
Interested In Learning How VanishIDs Solution Can Help?
Fill out the form, and one of our experts will get in touch.
Sources
- Cyberscoop. (2025, March 18). Infostealers fueled cyberattacks and snagged 2.1B credentials last year. Retrieved from https://cyberscoop.com/infostealers-cybercrime-surged-2024-flashpoint/
- Kaspersky. (2024, April 2)Data-stealing malware infections increased sevenfold since 2020, Kaspersky experts say. Retrieved from https://www.kaspersky.com/about/press-releases/data-stealing-malware-infections-increased-sevenfold-since-2020-kaspersky-experts-say/
- Medium. (2022, September 6). How Scammers Are Stealing Your Crypto With RedLine Malware. Retrieved from https://slowmist.medium.com/how-scammers-are-stealing-your-crypto-with-redline-malware-5f246c03bb67/
- CISA. (n.a). Threat Actors Deploy LummaC2 Malware to Exfiltrate Sensitive Data from Organizations. Retrieved from https://www.cisa.gov/news-events/cybersecurity-advisories/aa25-141b/
Matias Comella
Director of Marketing, VanishID
Matias is a cybersecurity marketing veteran with 25 years of experience across demand generation, brand marketing, and product marketing. Driven by his passion for information security, he spent a decade at a Fortune 500 cybersecurity giant and has since worked with various early-stage startups, helping transform cutting-edge security innovations into market successes.
All Posts
