Social engineering is the art of manipulating people into giving up confidential information, often by posing as a trusted source.
Phishing is a common form of social engineering that involves deceptive emails, messages, or websites designed to trick you into revealing passwords, financial data, or other sensitive details.
As threat actors become more sophisticated, both individuals and organizations face increasing security risks. These include fake tech support calls, convincing emails pretending to be from a bank, and other alarmingly persuasive forms that often lead to huge reputation damage and financial losses.
So, how can you protect yourself from social engineering attacks? You need to be aware of the tactics commonly used by threat actors to easily identify threats and follow recommended safety habits supported by advanced security tools. More details below!

What Is Social Engineering?
Social engineering is a type of cyber attack that relies on human interaction and deception rather than technical hacking. Instead of exploiting software vulnerabilities, attackers manipulate people into giving away access, credentials, or sensitive information.
Social engineering mostly plays on trust, urgency, and fear to trick victims into taking harmful actions, typically without realizing it.
You’ve likely seen it in everyday life: a fake email from your bank, a “tech support” pop-up urging you to call, or a coworker’s compromised account asking for login info. These are all examples of social engineering in action.
📩 Social Engineering Example
Subject: ⚠️ Urgent: Unusual Login Attempt Detected on Your Account
From: [email protected]
To: [Your Email Address]
Date: Mon, July 7, 2025, 8:15 AM
Dear Customer,
We’ve detected a suspicious login attempt on your account from an unrecognized device in London, UK, on July 8 at 2:03 AM GMT.
If this was not you, we strongly recommend that you verify your identity immediately to prevent unauthorized access.
Please click the link below to secure your account:
👉 Verify Account Now
Failure to act within 24 hours may result in a temporary suspension for your protection.
Thank you,
Security Team
YourBank Online Services
🔺 Red Flags to Notice
- Slightly off sender address
- Urgent tone and time pressure
- Suspicious link URL
- Generic greeting (“Dear Customer”)
Is Phishing Social Engineering?
Yes, phishing is a form of social engineering—one of the most widespread and dangerous ones. It involves tricking people into revealing sensitive information by posing as a legitimate entity, often through fake emails or websites.
Phishing comes in several variations, including:
- Spear phishing targets specific individuals or organizations with personalized messages, making the scam more convincing.
- Vishing (voice phishing) uses phone calls or voicemails to impersonate authority figures, like tech support or a bank.
- Smishing (SMS phishing) delivers fraudulent links or urgent messages via text.
What connects them all is their goal: to get you to act without thinking—clicking a link, sharing a password, or transferring money.
📨 Spear Phishing Example
Subject: Action Required: Updated Q3 Budget File for Review
From: [email protected]
To: [email protected]
Date: Tuesday, July 9, 2025, 9:42 AM
Hi Michael,
As discussed in last week’s team call, I’ve attached the revised Q3 budget file for your approval before we forward it to operations. Please review it by EOD and let me know if you have any changes.
Download Budget_Q3_2025.xlsx
Thanks,
Danielle Hartman
Sr. Finance Analyst
Finance Department
🔺 What Makes This Spear Phishing?
- It uses the recipient’s real name and job context.
- Refers to a recent meeting to build credibility.
- Uses a convincing corporate-style email address.
Includes a malicious link disguised as a work document.
How Social Engineering Works
Social engineering attacks follow a deliberate, step-by-step process designed to exploit human behavior. Here’s how they typically work:
1. Research
The attacker gathers publicly available information about the target, such as social media profiles, job roles, or company websites. They also often monitor the dark web to find data from previous breaches or obtained in other illegal ways. The goal is to understand what the victim values, whom they trust, and how they communicate.
2. Engagement
Next, the attacker initiates contact, often posing as a trusted entity like an IT admin, coworker, or customer service rep. They use the details collected earlier to sound convincing and authentic.
3. Exploitation
Once trust is established, the attacker manipulates the victim into taking action. This could involve clicking a malicious link, entering login credentials on a fake website, or downloading malware.
4. Execution
With the victim’s unconscious help, the attacker gains access to systems, data, or networks. From there, they may escalate privileges, steal confidential files, or plant ransomware.
Real-World Social Engineering Examples
- RSA Breach (2011): Attackers sent a phishing email titled “2011 Recruitment Plan” to RSA employees. A single click on a malicious Excel file allowed hackers to steal data that compromised the company’s two-factor authentication products.
- Nigerian Prince Scam: A classic long con where a “prince” promises riches in exchange for help transferring funds. Despite sounding obvious, it works by preying on greed and emotional vulnerability, demonstrating just how effective social manipulation can be.
Types of Social Engineering Attacks
Social engineering isn’t limited to just one tactic. Attackers use a variety of methods to exploit human behavior even more effectively without getting caught.
Let’s take a look at the most common types with examples you’ll likely recognize:
1. Phishing and Spear Phishing
As mentioned before, phishing uses fake emails, websites, or messages that look legitimate but are designed to steal personal data. These often urge you to “verify your account” or “reset your password.”
Example: An email claiming to be from your bank asks you to log in via a link that leads to a fake site.
Spear phishing is more targeted. Attackers check your digital footprint more carefully and personalize messages using information like your name, company, or recent activities to appear credible.
Example: A message from “your manager” asking for a file or login credentials.
2. Vishing and Smishing
Vishing (voice phishing) involves calls pretending to be from banks, IRS agents, or tech support, urging you to act quickly.
Example: “There’s suspicious activity on your card. Please confirm your account number to secure it.”
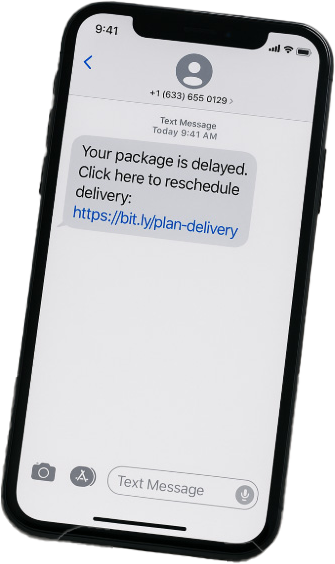
Smishing uses SMS messages with malicious links or fake login prompts.
Example: “Your package is delayed. Click here to reschedule delivery.”
3. Baiting
This tactic lures victims with something tempting, usually for free.
Physical Example: A malware-infected USB drive labeled “Confidential” left in a parking lot, waiting to be plugged in.
Online Example: A fake website offering free movie downloads or gift cards in exchange for your login info.
4. Pretexting
Attackers create a false scenario to trick someone into giving up information or access, which can be particularly risky for executives’ cybersecurity.
Example: Someone calls pretending to be from HR needing to “verify” your employee ID or Social Security number.
5. Quid Pro Quo
This scam promises a benefit in exchange for sensitive access or action.
Example: An attacker poses as IT support and offers to “fix” a system issue by asking the user to install remote-access software.
6. Tailgating
This is a physical social engineering attack that is often overlooked. It involves following someone to a restricted area.
Example: A person without credentials follows an employee into a secure office building by pretending to have forgotten their badge or carrying coffee to appear non-threatening.
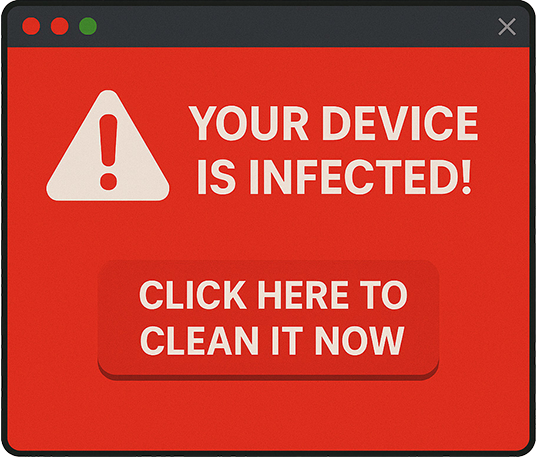
7. Scareware
Scareware bombards users with alarming messages to force them into unsafe decisions.
Example: A pop-up warning: “Your device is infected! Click here to clean it now!”—which actually installs malware.
How to Identify a Social Engineering Attack
Social engineering scams are designed to manipulate your emotions and instincts, not just your technology. Recognizing the red flags can help you stop an attack before it starts.
Here are the most common psychological cues to watch for:
Urgency
Attackers often pressure you to act quickly, before you have time to think, by triggering a fear-based reaction.
Example: “Your account will be locked in 10 minutes unless you confirm your identity now.”
This tactic bypasses critical thinking by triggering a fear-based reaction.
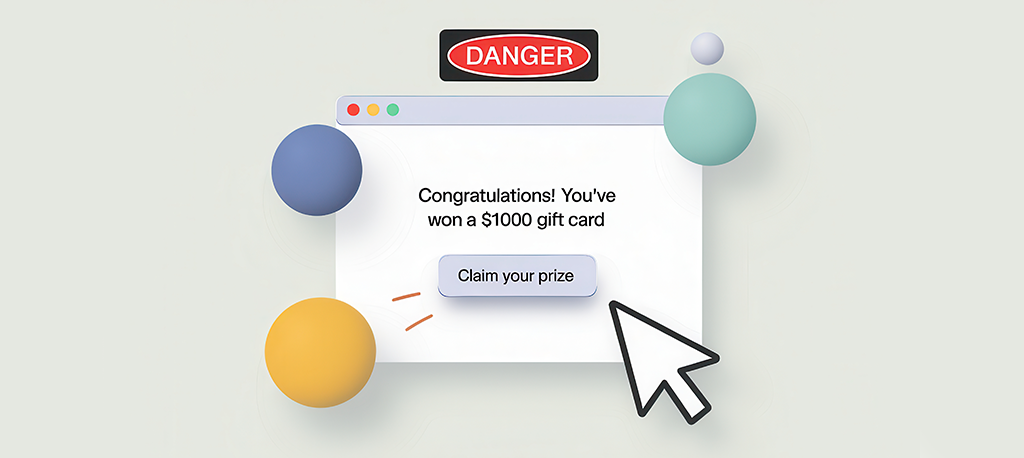
Emotional Appeals
Threat actors exploit your emotions to lower your guard and prompt impulsive decisions.
Fear: “Your device is infected! Click to clean it immediately.”
Excitement: “Congratulations! You’ve won a $1000 gift card!”
Guilt: “This is your coworker Bill. I lost access, so can you send me the file again?”
Suspicious Requests for Sensitive Data
If someone unexpectedly asks for login credentials, account numbers, or personal details (especially via email, phone, or text), it’s likely a social engineering scam.
No legitimate company or IT department will ever ask for this kind of information in unsecured formats.
Example: “We detected a login issue. Please reply with your password to confirm your identity.”
How to Prevent Social Engineering Attacks
By changing your everyday habits and applying safety measures, you can improve social engineering prevention at home, at work, or anywhere else. Some of the most effective strategies include:
1. Secure Communication Habits
Staying more cautious about your communication is one of the most effective ways to stop social engineering attacks in their tracks. Here’s how:
Never click on suspicious links:
- If a message seems off, don’t interact with it—type the URL manually or make sure with the person or provider who is mentioned as the sender that it is actually from them.
- Hover over links to see where they really lead.
Use official contact channels:
- Got a message from your “bank” or IT team? Don’t reply directly. Instead, call the number listed on the official website or log in through your verified portal.
- Avoid using the contact info provided within the suspicious message itself.
Be cautious with email attachments:
- If you weren’t expecting a file (even from someone you know), double-check before opening it.
- When in doubt, ask the sender to verify via a separate communication channel (e.g., call or message outside of email).
🔎 Pro Tip: Look for red flags like misspellings, odd greetings, or urgent demands, as they can be signs of social engineering scams.
2. Strengthen Account Security
Strong account security can prevent attackers from proceeding further, even if they trick you into revealing personal information.
Enable multi-factor authentication (MFA):
- MFA requires a second step (like a code sent to your phone or a biometric scan) even if someone knows your password.
- Use app-based authenticators (e.g., Google Authenticator, Authy) rather than SMS when possible for added security.

Use strong, unique passwords:
- Avoid predictable choices like “Password123” or using the same password across multiple sites.
- A strong password should include a mix of uppercase, lowercase, numbers, and symbols, and be at least 12 characters long.
Employ a password manager:
- Password managers like 1Password, Bitwarden, or LastPass generate and store strong, unique passwords for each of your accounts.
- This keeps your credentials secure and means you only have to remember one master password.
🛡️ Security Tip: If you suspect your credentials were exposed in a phishing attempt, change your password immediately and check for unusual activity.
3. Protect Your Digital Footprint
Social engineers often rely on publicly available information to make their scams more easily believable.
The more you share online, the easier it becomes for them to exploit you, so proper digital footprint protection is essential.
Limit what you share on social media:
- Avoid posting travel plans, job updates, or family details that could help scammers guess your routines or build convincing stories.
- Oversharing makes it easier for attackers to impersonate you or trick you with a tailored phishing attempt.
Adjust your privacy settings:
- Set your social media profiles to “friends only” or private.
- Carefully select who you connect with online, especially on professional platforms like LinkedIn.
Watch out for security question clues:
- Don’t post information like your mother’s maiden name, your first pet’s name, or the city you were born in. These are commonly used as account recovery questions.
💻 Did You Know? Attackers often “stalk” their victims’ digital lives before making contact, just like a con artist researching a mark. By limiting what’s available about you online, you make it much harder for them to profile and trick you.
4. Build a Culture of Verification
Social engineers exploit trust the most, so you need to develop a habit (both personally and professionally) of verifying before trusting.
This is especially important in environments where sensitive data or financial access is involved.
Always verify identity (online and offline):
- If someone approaches you in person claiming to be from IT, maintenance, or a delivery service, ask for an official ID. Don’t let anyone into secure areas without proper authorization.
- No badge? No entry. If someone forgets it, their identity needs to be confirmed by a trusted individual who can recognize them.
Confirm phone calls and emails through official channels:
- Never trust the contact details provided in a suspicious message. Instead, look up the contact independently using your organization’s directory, a verified website, or previously confirmed info.
- If a caller asks for login credentials or payment approval, hang up and verify their identity separately.
Educate employees and family members:
- Regularly train your team to recognize red flags and respond safely.
- Invest in advanced digital protection for executives and senior staff, as they’re frequent targets due to their access and visibility.
- At home, teach your family (especially kids and elders) not to respond to random “tech support” calls or prize giveaways.

🧠 Pro Tip: Social engineering attacks often succeed because people don’t want to seem rude or paranoid. But in cybersecurity, a little skepticism is healthy—and necessary.
5. Safeguard Devices and Networks
Even the best habits can’t protect you if your devices and networks are exposed. You can take multiple steps to block social engineering attempts at the technical level, such as:
Keep software and firmware up to date:
- Regular updates patch known vulnerabilities that attackers often exploit.
You don’t have to remember about it, but just enable automatic updates for your operating system, apps, browsers, and even smart devices.
Use comprehensive security solutions:
- Install reputable antivirus and anti-malware software across all your devices.
- Enable firewalls, spam filters, and browser protection features to detect threats early and act before they escalate.
Avoid unsecured public Wi-Fi:
Hackers can intercept your data on open networks (like those in airports or coffee shops).
If you must use public Wi-Fi, connect through a VPN (Virtual Private Network) to encrypt your activity.
Physically secure your devices:
- Lock your screen when stepping away, no matter where you are.
- Never leave laptops or phones unattended in public spaces, and consider full-disk encryption for extra protection.
🔐 Security Reminder: Many social engineering attacks are multi-layered, starting with a message but ending in device compromise. Securing your hardware and network closes one of their favorite doors.
Responding to a Suspected Attack
Even with the best precautions, social engineering attacks can still slip through. If you suspect you’ve been targeted (or worse, taken the bait already), acting quickly can limit the damage. Follow these steps immediately:
Step 1: Disconnect and Stop Communication
- Do not engage further with the attacker. Close the email, hang up the call, or exit the site.
- If you clicked a suspicious link or downloaded a file, disconnect your device from the internet to prevent further data leaks.
Step 2: Change Your Passwords
- Immediately change the password of any account you think may be compromised.
- Start with email, banking, and work accounts, then others.
- Use a strong, unique password, and enable multi-factor authentication if you haven’t already.
Step 3: Alert Your IT or Security Team
- If it happened at work, report the incident to your IT or cybersecurity team right away.
- The sooner they know, the faster they can isolate threats, check for breaches, and support you.
Step 4: Monitor Accounts for Suspicious Activity
- Watch for unauthorized logins, strange emails, or account changes in the days that follow.
- Set up security alerts or use tools that notify you of new sign-ins or password changes.
Step 5: Report the Incident
- For phishing, fraud, or identity theft, report the attack to:
- Local authorities or your country’s cybercrime unit
- Your bank or credit card provider (if financial info was involved)
- Platforms like the FTC (U.S.), Action Fraud (UK), or the Anti-Phishing Working Group.
Real-World Examples and Lessons Learned
Social engineering has taken down some of the world’s biggest names, and saved others who acted fast.
- In 2020, Twitter (now X) experienced a major breach when attackers used phone-based spear phishing (vishing) to trick employees into providing internal credentials. The result? High-profile accounts, including those of Elon Musk, Barack Obama, and Apple, were used in a Bitcoin scam. The incident highlighted the importance of access controls and employee verification procedures, which Twitter later strengthened to prevent future attacks.
- By contrast, a Google employee once avoided compromise thanks to multi-factor authentication (MFA). Although the attacker successfully mimicked a company login page, the absence of the second authentication factor stopped the breach in its tracks.
The takeaway? Preparedness and verification practices work. The organizations that recover fastest are the ones that trained, planned, and stayed alert.
Conclusion
Social engineering attacks are not just technical threats, as they also strongly depend on psychological factors.
Staying safe online means staying vigilant, informed, and proactive. If you learn to recognize manipulations and apply smart safety habits, you can drastically reduce your risk of falling victim.
Remember to think twice before clicking links, verify requests (even from people you know), and protect your digital footprint. Simple actions like enabling multi-factor authentication and using a password manager go a long way.
For more tips, explore trusted resources like CISA.gov, FTC.gov, or your country’s national cyber agency.
If you’re serious about securing your identity and digital footprint, VanishID can help. Our tools are designed to monitor threats, reduce digital exposure, and give businesses real control over their employees’ personal information.
🔒 Take control of online safety in your company—start with VanishID.